Only /Data Should be Writable
A key principle of security is reducing the attack surface. In mojoPortal Content Management System the only folder that needs to be writable by the web process is the /Data folder. You should make sure no other folders are writable. You should make sure all other folders are not writable by the web process.
The user that needs permissions is the user that is the identity on the application pool used by your site in IIS. On a Windows 2022 server, the way we do this is to grant the user Read permission to the root folder to provide read permissions to the entire web site. Then, we grant it Write and Modify on the /Data folder. This may be different in your environment and shared hosting will typically have some kind of control panel for managing permissions. In some hosting it may not be possible for you to tighten down the file system access as much as you would like. If that's your case, we suggest better hosting.
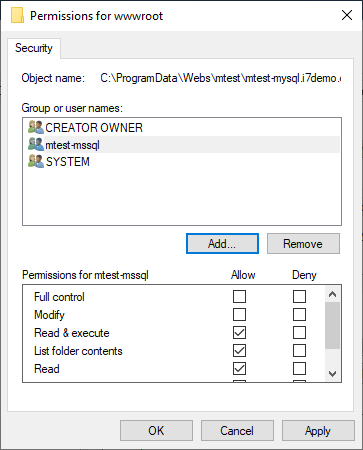 Proper wwwroot folder permissions
Proper wwwroot folder permissions
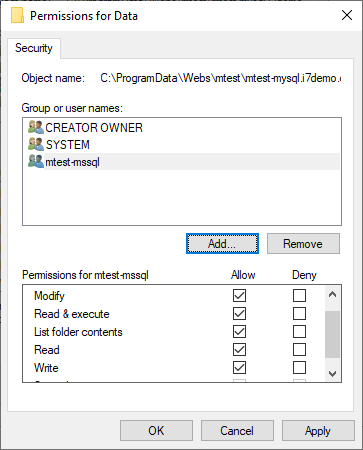 Proper data folder permissions
Proper data folder permissions
Note that in the example above mtest-mssql is the user that is the identity on the application pool, so that is the user whose permissions are being set. It may be a different user that is the identity on your application pool. Whatever user is the identity on your application pool, that is the user who needs permissions.
Remove Script and Execute Permissions from Writable Folders
The Data folder should not allow executing scripts or executables. If a user somehow manages to upload a malicious script or file, we don't want the web process to be able to run the script or execute the file.
To do this in IIS 7 or greater
- In IIS, in the left pane, click the plus sign next to your site to show all the folders, then click the Data folder
- In the middle pane double click "Handler Mappings"
- In the right pane click "Edit Feature Permissions"
- Un-check Script and Execute, then click OK